

Blockchain analysts from Match Programs have discovered that the Orbit Chain hackers used the identical techniques as these in a number of different high-profile assaults – suggesting {that a} cybercrime group, presumably the notorious Lazarus Group, stands behind these hacks.
This legal group appears to have been busy final yr. Cointelegraph cited a January 3, 2024, report by Match Programs, naming Coinspaid, Coinex, and Atomic Wallet among the many group’s victims.
Per the report,
“[The analysis] provides motive to imagine that the identical legal group could also be concerned within the hacking of the Orbit bridge, which in 2023 had beforehand dedicated a number of giant hacks of the cryptocurrency companies Atomic pockets, CoinsPaid, CoinEx, and so forth., utilizing instruments and patterns of the well-known Lazarus group.”
As the brand new yr approached, hackers exploited Orbit Bridge, the cross-chain bridging service of a South Korean-based multi-asset Orbit Chain, making off with $82 million.
Learn extra: Are Hackers Two Steps Ahead of Security in a Cat-and-Mouse Game? Experts Answer
Frequent Threads
The analysts discovered that the hackers used Twister Money. That they had gasoline funds from different accounts that withdrew them from the favored crypto mixer.
A mixer does ‘mixes’ completely different funds so as to obscure the path main again to the unique sources. Due to this fact, hackers use it to combine their identifiable funds with others’ funds.
That mentioned, Match System reportedly ‘de-mixed’ the funds utilizing specialised software program. It analyzed the “traits and patterns earlier than and after the Twister.money mixer, contemplating transaction volumes and dates/instances, in addition to different specialised strategies.”
What the group found was a bunch of addresses. Considered one of them used the SWFT protocol to switch funds to different addresses. The protocol was additionally used within the DFX Finance, Deribit, and AscendEX assaults.
Following the Oribit assault, a portion of the funds despatched by SWFT traveled by numerous chains, gathering in a Tron pockets. It was then transferred to an trade and cashed out.
One other widespread issue, the analysts argue, is that the attackers used Avalanche Bridge and Sinbad within the Orbit assault and several other earlier assaults.
Per the group,
“[These are] instruments and patterns of the well-known Lazarus group.”
Learn extra: Blockchain Association Sues OFAC Over Sanctions on Tornado Cash
Lazarus was Answerable for a Fifth of Complete Losses in 2023
The North Korea-affiliated hacker group Lazarus was answerable for $308.6 million stolen in 2023, the main bug bounty and safety companies platform Immunefi discovered. This can be a whopping 17% of the full yr losses.
The group was allegedly behind the high-profile assaults on Atomic Wallet, CoinEx, Alphapo, Stake, CoinsPaid, and the huge Ronin Network assault, ensuing in a $625 million loss.
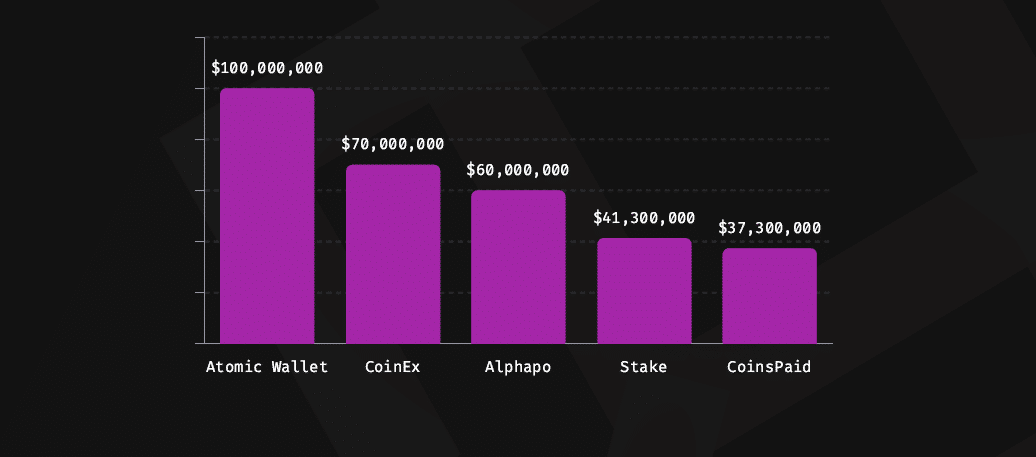
The Immunefi group not too long ago published a report focusing particularly on the Lazarus Group. It discovered that, between 2021 and 2023, the group stole $1,903,600,000 throughout the Web3 ecosystem.
In December, Immunefi CEO Mitchell Amador commented that,
“As we strategy 2024, their escalating sophistication is regarding. Their proficiency in exploiting infrastructure vulnerabilities, sensible contract weaknesses, in addition to their meticulous social engineering operations, underscores their emergence as maybe essentially the most urgent menace to web3 at this time.”
Learn extra: Record Losses in Web3 May Be Coming as Crypto Prices Rise: Immunefi



